The NTFS file system is used by default in Windows. And normally a file has only one associated normal data stream with the name :$DATA. But there are also the so-called “Alternate Data Streams” (ADS), which can contain additional data. These ADS are not visible in the Windows Explorer or most other applications.
ADS are sometimes used by the system, but could also be used by attackers to hide data.
Read NTFS Alternate Data Streams
Many web browsers on windows stamp downloaded files from the Internet with a “Mark of the web” (MOTW) in the Zone.Identifier stream. This stream contains information about the source of the file - e.g. that it was downloaded from the Internet.
To read the content of an ADS, you can simply use Get-Content with the -Stream parameter and the stream name. Alternatively, :<name of stream> can be appended to the file name.
| |
The actual content of Zone.Identifier can vary. Sometimes it contains more or less information. However, the information on the ZoneId should always be included. The following values are possible for the zone:
| Value | Meaning |
|---|---|
| 0 | My Computer |
| 1 | Local Intranet Zone |
| 2 | Trusted sites Zone |
| 3 | Internet Zone |
| 4 | Restricted Sites Zone |
The Windows Smartscreen Filter sometimes also creates its own ADS called SmartScreen. If it contains Anaheim, the file has been classified as unsafe.
| |
And if there are any other streams, you can of course read them using the same procedure.
Remove the Mark of the web
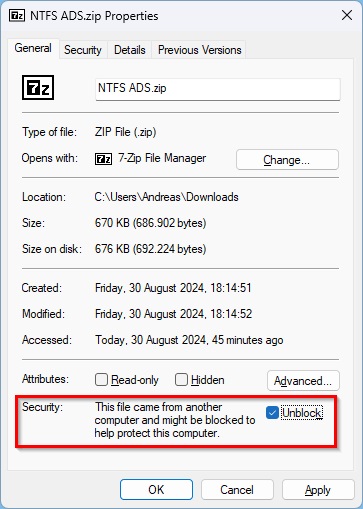
The regular way to remove the “Mark of the web” is via Unblock-File or via the properties dialog of the file.
| |
Find NTFS Alternate Data Streams
To find out which Alternate Data Streams are available, the -Stream parameter of the Get-Item cmdlet can be used. With * as a placeholder, we can find all ADS.
| |
We can also filter out the information that the standard :$DATA stream is available:
| |
With my Get-NTFSADS.ps1 script it’s even a bit easier and prettier. Check it out on Github.
Write NTFS Alternate Data Streams
It is possible to write your own data into ADS. For example, Set-Content/Add-Content can be used for this.
| |
Delete NTFS Alternate Data Streams
ADS can also be deleted via Remove-Item like normal files. The file and the :$DATA stream would continue to exist in the following example:
| |
Conclusion
NTFS Alternate Data Streams are an interesting function. They are less suitable as a gateway for attackers, as no additional data streams can be transferred during a normal download. However, ADS could still be transferred in some container formats, e.g. within .vhdx files for virtual hard disk images. However, the use of an ADS-capable container would also be very suspicious.
I think that ADS could rather be used by attackers if they have already infiltrated a system. Malicious code or other data could then be hidden. However, modern EDR solutions should (in my opinion) take action if ADS is used. Technically, this would be possible via Sysmon logging, for example.