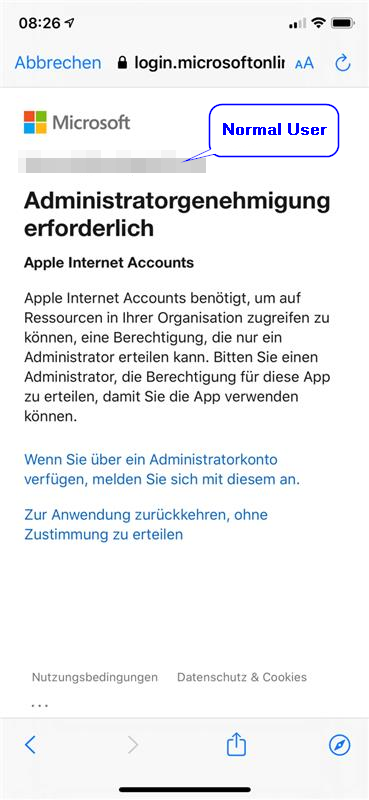
When the first users logged into Office 365 with his iPhone to sync his Contacts and Calendar, he got this dialogue:
Need admin approval Apple Internet Accounts Apple Internet Accounts needs permission to access resources in your organization that only an admin can grant. Please ask an admin to grant permission to this app before you can use it.
By the way, the app used to be called “iOS Accounts” and was apparently renamed in early 2020. However, the previous AppID has remained the same.
Cause
The following reasons have caused this message:
- Apple Internet Accounts app is required by Apple iOS to access the user’s Office 365 resources. Access to resources of an Office 365 Tenant by a third-party app is only possible after explicit approval.
- No user or administrator approval has yet been granted for Apple Internet Accounts in this tenant.
- The user approval is deactivated tenant wide. This recommended setting can be set so that end users cannot simply authorise third-party apps to access company data.
You can find that setting for 3. in Azure AD under “Enterprise applications” -> “User settings”. The option is called “Users can consent to apps accessing company data on their behalf”. This setting should be kept to “No”! The fact that the end user is not allowed to allow any apps (and therefore can’t get ahead here) is exactly what you want to protect company data from unauthorized access.
Solution
There are several possible solutions without simply unlocking all third-party apps.
Solution approach
Update 2022-06-20: It’s usually not necessary anymore to craft the url manually. Instead you can just click this link: https://aka.ms/ConsentAppleApp. Steps 1 and 2 can be skipped then.
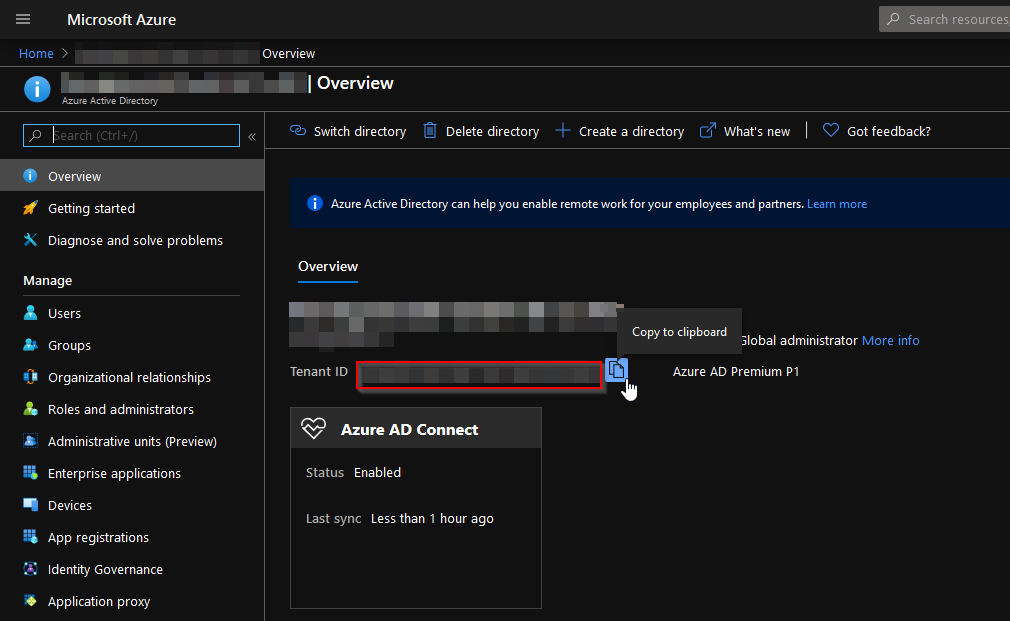
Step 1: Find out TenantID
First of all you have to find out the Tenant ID of the Azure AD Tenant. You’ll find it on the “Overview page in Azure Active Directory” (marked red in the following screenshot).
Step 2: Craft URL
The placeholder <TenantID> has to get replaced with the actual TenantID from Step 1 in the following URL. The generated URL can then be accessed with Tenant Admin (Global Administrator) rights. The client_id in the URL is the ID of Apple Internet Accounts.
| |
Step 3: Grant permission as admin for the whole Tenant
The query “Permission requested - Accept for your organization - Apple Internet Accounts” must be confirmed with “Accept”.
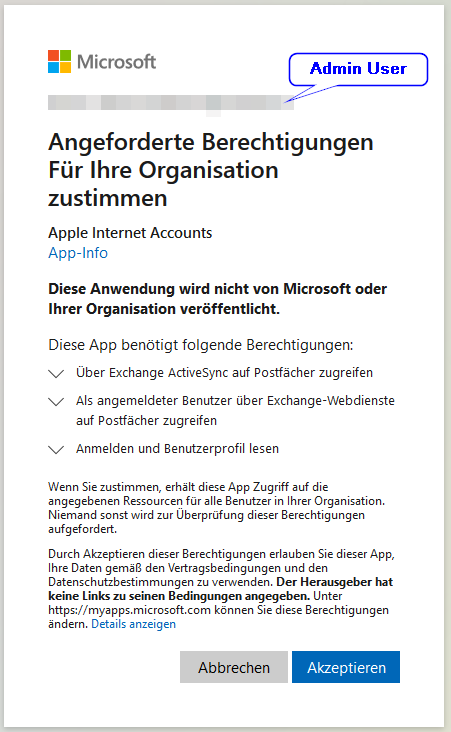
If you crafted the URL as described in Step 1 and 2, you’ll receive an error now, because the redirect URL points to https://example.com. The error AADSTS900561 may be ignored in this case.
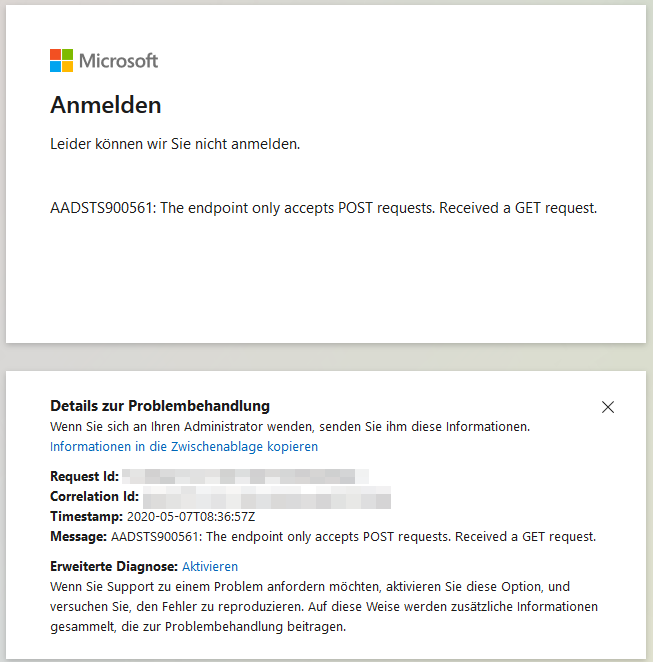
The app should be listed in Azure AD under “Enterprise applications” -> “All applications” now.
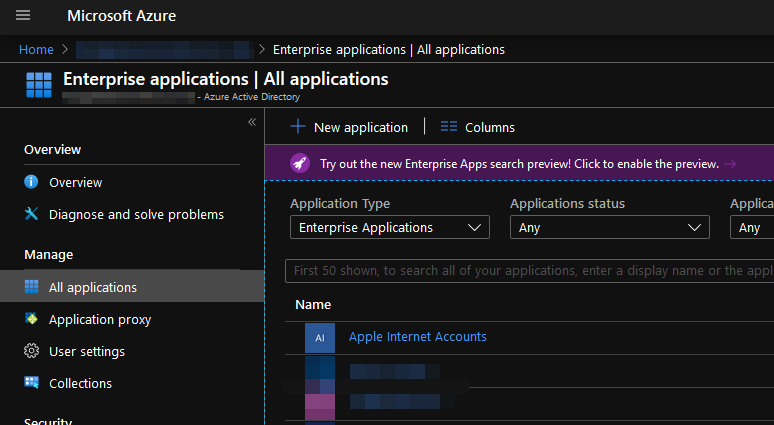
Step 4: Test if it works
Afterwards the users should be able to access their Calendar/Contacts in Exchange Online using iOS.
Solution approach 2: Enable Administrator Consent request
Alternatively, you can activate that users can request the approval of an app. This is also possible in addition to the one-time administrative approval from solution 1.
Step 1: Enable Admin Consent Requests
Open “Enterprise applications” -> “User settings” in Azure AD as an Administrator. Under “Admin consent requests (Preview)” you can enable the option “Users can request admin consent to apps they are unable to consent to”. Then click on “Select admin consent request reviewers” and select the Administrators, that should approve the requests. If required, you can enable to notify these administrators by email. In Default the requests expire after 30 days, which can be adjusted aswell.
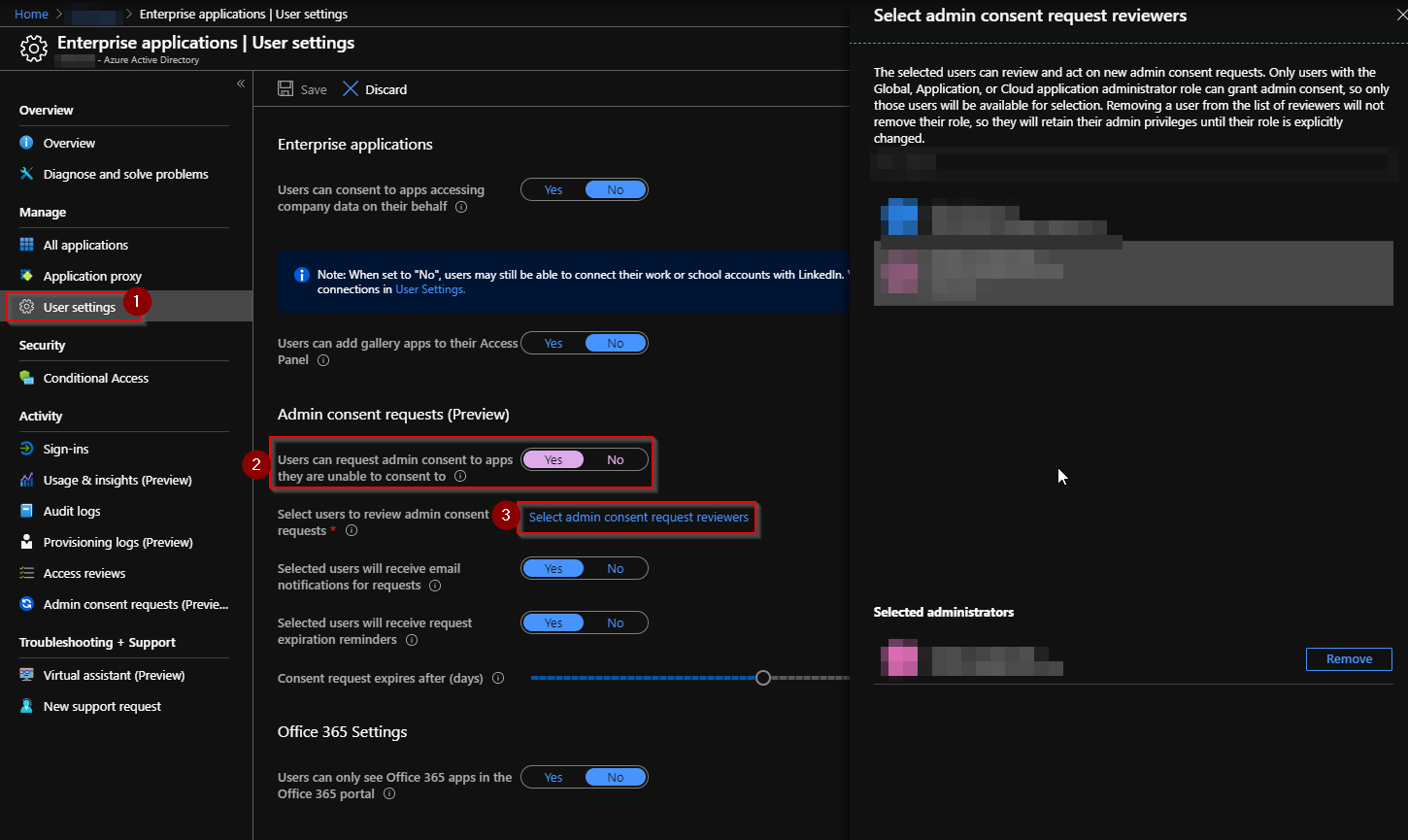
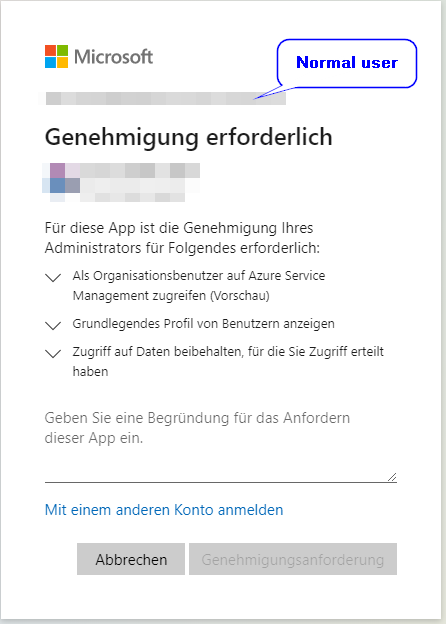
Step 2: User requests Administrator-Consent
When a users wants to use a new app, he’ll receive the info “Approval Required”. The necessary permissions of the app are listed. The user must enter a reason for the application request. The approval request can then be sent.
Step 3: Administrator reviews the Approval Request
The selected admins receive an E-Mail, which lists the details of the request. In that E-Mail they can click on “Review Request”, to review more details. If they don’t act until the expiration date, the request will get rejected automatically.
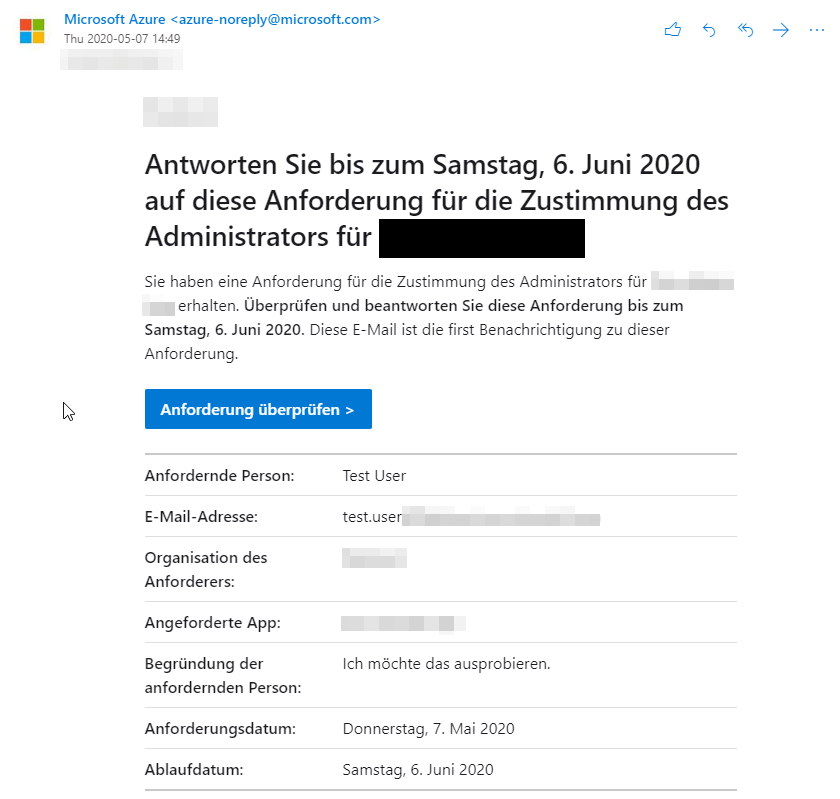
Alternatively the Administrator can review the list of open requests in Azure AD. Open “Enterprise applications” -> “Admin consent requests” to do so.
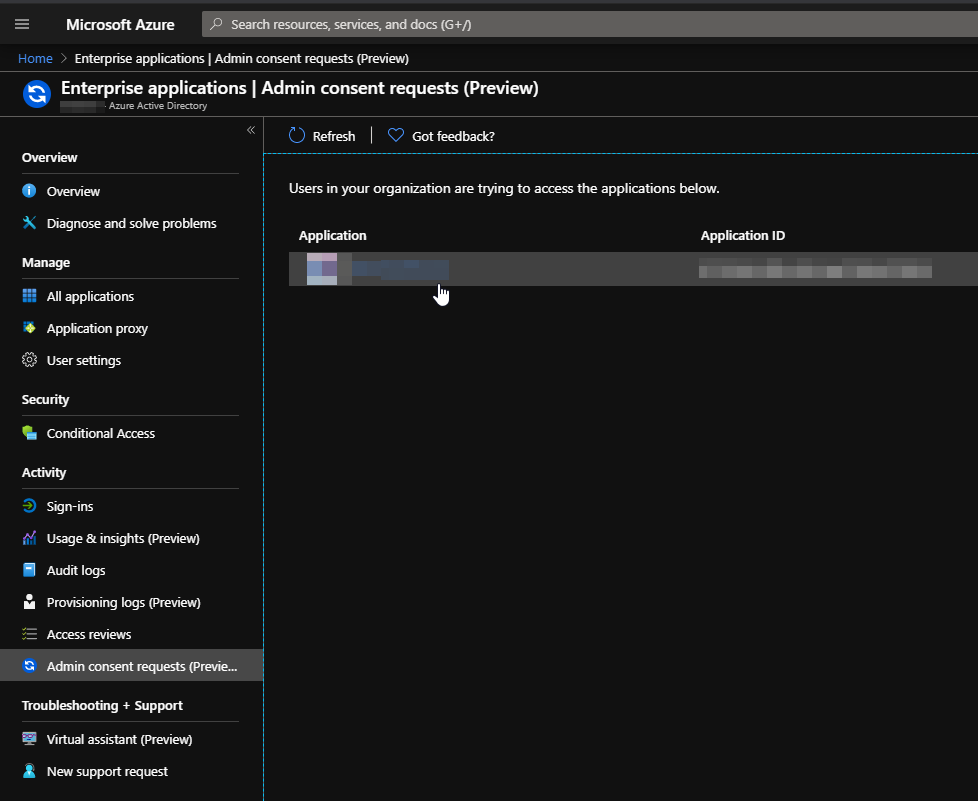
Details like Name, Homepage URL, used Reply URLs can get reviewed. Under “Requested by” it lists the requesting user. The Administrator can review the permissions and approve the request (“Review permissions and consent”) or “Deny” it. If the application should get blocked permanently, you can select “Block” - no further requests for this app are possible then.
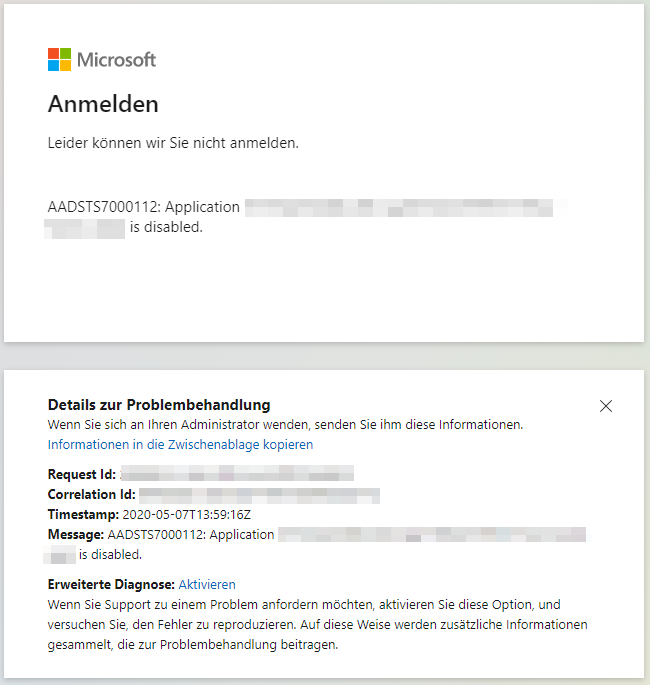
If the application was not approved, the user would get the message AADSTS7000112, when trying to use it next time.
Step 4: Test if it works after the consent
Afterwards the users should be able to use the requested and approved App.
Disable an App that was allowed before
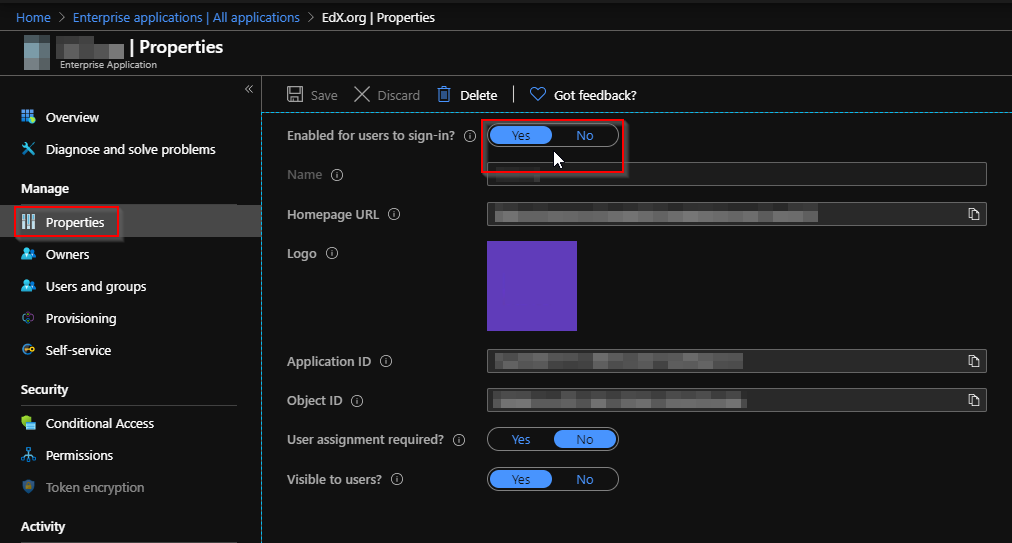
If an app has already been allowed, it can be deactivated again if required. To do this, select the application from “Enterprise applications” and under “Properties” set the option “Enabled for users to sign-in” to “No”. If you click on “Delete” here instead, the users can request approval again.